Certificates: Difference between revisions
(REworked) |
(concise-gpt) |
||
| Line 1: | Line 1: | ||
[[Category:Server]] | [[Category:Server]] | ||
=Certificate | = Certificate-Based Authentication = | ||
Bondix | Bondix offers the capability to authenticate incoming tunnel connections using certificates. This method eliminates the need for manual tunnel creation for each device on the server. By creating a root certificate and signing client certificates with it, the server can automatically generate ad-hoc tunnel configurations for incoming connections, enhancing scalability. | ||
For guidance on configuring the SSL certificate on your Bondix server, please refer to: [[Server_Certificates_with_LetsEncrypt|Server Certificates]]. | |||
== Prerequisites == | |||
=== Setting Up Certificates === | |||
The Bondix server includes scripts within the .ssl subdirectory for certificate setup: | |||
cd /opt/bondix/server/ssl | cd /opt/bondix/server/ssl | ||
./create-server-cert.sh | ./create-server-cert.sh | ||
This script | This script generates a self-signed server certificate and a root certificate for client certificate signing. It is executed automatically post-installation. Ensure the presence of `client-root.key` and `client-root.crt` in the .ssl subdirectory; if absent, rerun the script. | ||
Apply this parameter where necessary, considering multiple listeners or separate ports for different services. Note that adding this authentication method has no effect where incoming tunnels are not allowed. Restart the server with `systemctl restart bondix` to apply changes. | |||
=== Generating a Client Certificate === | |||
Generate client certificates using a script located in the ssl server subfolder: | |||
cd /opt/bondix/server/ssl | |||
./create-client-cert.sh <TunnelName> | |||
Ensure the script is executed in the intended directory and that <TunnelName> is distinct for each certificate. The script outputs a certificate and key pair in `./ssl/clients/`. | |||
=== Configuring the Client for Certificate Authentication === | |||
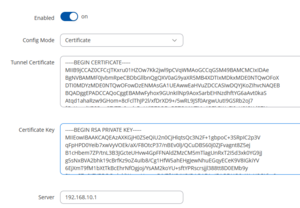
[[File:Client Certificate Config.png|thumb|Client Certificate Auth configuration]] | |||
On the client side, select 'Certificate' as the 'Config Mode' and input the generated certificate/key pair. Additionally, configure the server's hostname or IP address. The tunnel will then appear on the server without requiring further setup. | |||
=== | = Additional Options = | ||
== Setting Up Tunnel Limits == | |||
To manage the number of clients connected to the server when using certificate authentication, introduce a soft limit on the total active tunnels with the following configuration in /etc/saneserver.json: | |||
```json | |||
{"target": "tunnel", "action": "set-tunnel-limit", "maxTunnel": 100, "gracePeriod": 30}, | |||
* `maxTunnel` determines the maximum active tunnels. Exceeding this limit prompts tunnels to connect to an alternate server, configured either as a secondary server on the client or through a hostname with multiple IP records. | |||
* `gracePeriod` is the duration in seconds allowing a previously rejected tunnel to reconnect without denial, ensuring connectivity even when resources on secondary servers are unavailable. | |||
= | == Auto-Removing Stale Certificate Tunnels == | ||
To address fluctuation in tunnels utilizing certificate authentication, enable automatic tunnel removal with the following addition to /etc/saneserver.json: | |||
```json | |||
{"target": "tunnel", "action": "set-tunnel-autoremove", "enabled": true, "timeout": 600} | |||
* `timeout` sets the lifespan of a certificate-based tunnel on the server in seconds, facilitating the management of active tunnels. | |||
After making changes to `/etc/saneserver.json`, the service must be restarted via `systemctl restart bondix`. | |||
Revision as of 00:11, 8 February 2024
Certificate-Based Authentication
Bondix offers the capability to authenticate incoming tunnel connections using certificates. This method eliminates the need for manual tunnel creation for each device on the server. By creating a root certificate and signing client certificates with it, the server can automatically generate ad-hoc tunnel configurations for incoming connections, enhancing scalability.
For guidance on configuring the SSL certificate on your Bondix server, please refer to: Server Certificates.
Prerequisites
Setting Up Certificates
The Bondix server includes scripts within the .ssl subdirectory for certificate setup:
cd /opt/bondix/server/ssl ./create-server-cert.sh
This script generates a self-signed server certificate and a root certificate for client certificate signing. It is executed automatically post-installation. Ensure the presence of `client-root.key` and `client-root.crt` in the .ssl subdirectory; if absent, rerun the script.
Apply this parameter where necessary, considering multiple listeners or separate ports for different services. Note that adding this authentication method has no effect where incoming tunnels are not allowed. Restart the server with `systemctl restart bondix` to apply changes.
Generating a Client Certificate
Generate client certificates using a script located in the ssl server subfolder:
cd /opt/bondix/server/ssl ./create-client-cert.sh <TunnelName>
Ensure the script is executed in the intended directory and that <TunnelName> is distinct for each certificate. The script outputs a certificate and key pair in `./ssl/clients/`.
Configuring the Client for Certificate Authentication
On the client side, select 'Certificate' as the 'Config Mode' and input the generated certificate/key pair. Additionally, configure the server's hostname or IP address. The tunnel will then appear on the server without requiring further setup.
Additional Options
Setting Up Tunnel Limits
To manage the number of clients connected to the server when using certificate authentication, introduce a soft limit on the total active tunnels with the following configuration in /etc/saneserver.json:
```json {"target": "tunnel", "action": "set-tunnel-limit", "maxTunnel": 100, "gracePeriod": 30},
- `maxTunnel` determines the maximum active tunnels. Exceeding this limit prompts tunnels to connect to an alternate server, configured either as a secondary server on the client or through a hostname with multiple IP records.
- `gracePeriod` is the duration in seconds allowing a previously rejected tunnel to reconnect without denial, ensuring connectivity even when resources on secondary servers are unavailable.
Auto-Removing Stale Certificate Tunnels
To address fluctuation in tunnels utilizing certificate authentication, enable automatic tunnel removal with the following addition to /etc/saneserver.json:
```json {"target": "tunnel", "action": "set-tunnel-autoremove", "enabled": true, "timeout": 600}
- `timeout` sets the lifespan of a certificate-based tunnel on the server in seconds, facilitating the management of active tunnels.
After making changes to `/etc/saneserver.json`, the service must be restarted via `systemctl restart bondix`.