Transparent Bonding Proxy: Difference between revisions
No edit summary |
No edit summary |
||
| Line 7: | Line 7: | ||
=== Prerequisites === | === Prerequisites === | ||
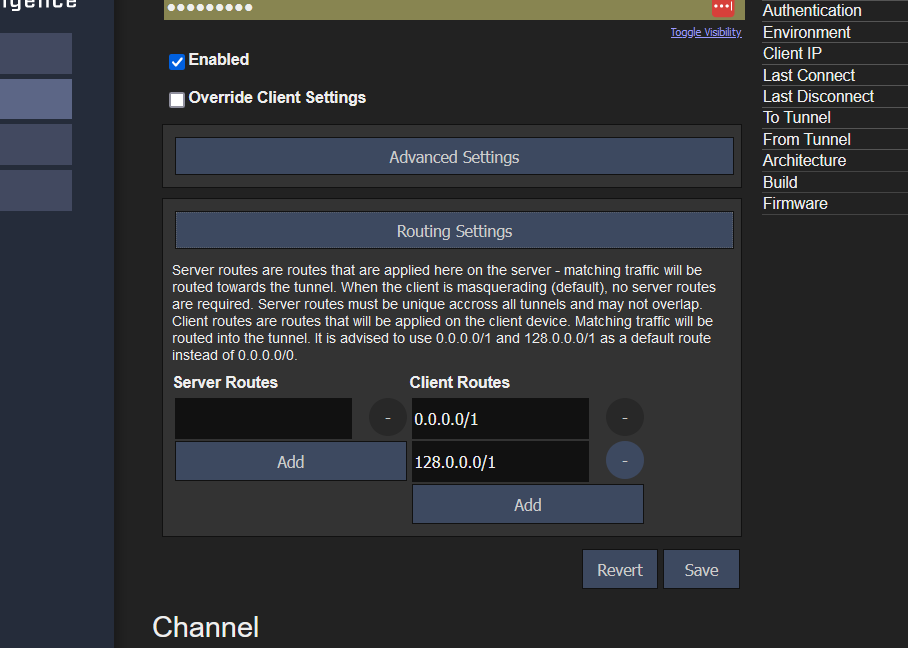
TBP only works with server routes and masquerading disabled on the client. | TBP only works with server routes and masquerading disabled on the client. | ||
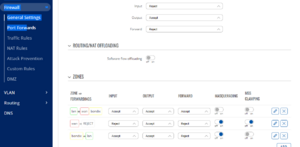
[[File:Tbp-prerequisites-1.png| | [[File:Tbp-prerequisites-1.png|frameless|Where to find the masquerading option in a Teltonika router]] | ||
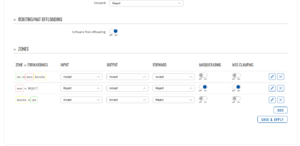
[[File:Tbp-prerequisites-2.png| | [[File:Tbp-prerequisites-2.png|frameless|Masquerading turned off]] | ||
SANE server uses IP_TRANSPARENT to bind to non-local IP addresses, which required CAP_ADMIN capabilities. For proper operation, we must identify traffic that matches our Bonding Proxy connections: | SANE server uses IP_TRANSPARENT to bind to non-local IP addresses, which required CAP_ADMIN capabilities. For proper operation, we must identify traffic that matches our Bonding Proxy connections: | ||
Revision as of 10:58, 23 June 2023
Transparent Bonding Proxy
Transparent Bonding Proxy (TBP) as a work in progress extension that allows Bonding Proxy to establlish connections using the client's original IP. Without TBP, connections utilizing Bonding Proxy will always use the server's default IP address, even if subnets are properly routed to a client.
Transparent Bonding Proxy is currently under development and has been added in snapshot versions starting 20230426.
Prerequisites
TBP only works with server routes and masquerading disabled on the client.
SANE server uses IP_TRANSPARENT to bind to non-local IP addresses, which required CAP_ADMIN capabilities. For proper operation, we must identify traffic that matches our Bonding Proxy connections:
# iptables -t mangle -N DIVERT # iptables -t mangle -A PREROUTING -p tcp -m socket -j DIVERT # iptables -t mangle -A DIVERT -j MARK --set-mark 1 # iptables -t mangle -A DIVERT -j ACCEPT
Then, create a routing table that defines your routed subnet(s) as local
# ip rule add fwmark 1 lookup 100 # ip route add local 0.0.0.0/0 dev lo table 100
0.0.0.0/0 allows any IP to be used. While this also works, it has security implications - add your routed subnets instead to minimize risks.
Currently, TBP will be activated for any proxy connection initiated by a client with a routed IP.
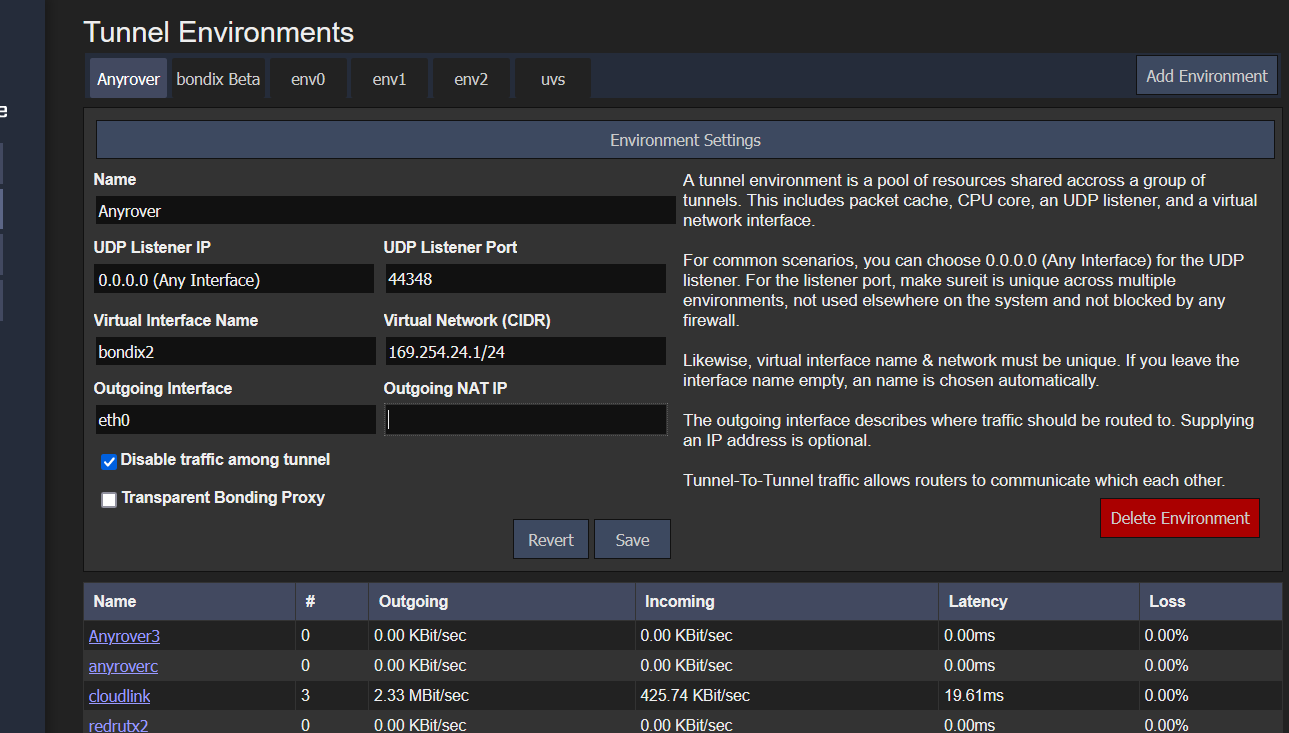
If "Outgoing NAT IP" is configured in the tunnel's environment settings, this IP will be used for masquerading instead. Please make sure it is empty if you want to use TBP.
| ⚠️ | Please note that the smallest public IP network you can route is a /31 (2 usable IP addresses)! |
|---|
Known issues
- When a daemon on the server is listening on 0.0.0.0 (any IP), this will take precedence over incoming connections targetting a target in your subnet. saneserver's current default configuration is doing exactly that.