DMZ and 1:1 NAT configuration: Difference between revisions
(Created page with "= DMZ and 1:1 NAT configuration with additional static, public IPv4 addresses on the Bondix server = This page describes how to forward traffic from a public IP on the Bondix server to a LAN host behind an Bondix client router using iptables and port forwarding. == Assumptions == * You are operating an own Bondix server with the option to get additional public IPv4 addresses. * You have an additional IP address on the Bondix server (example: ''14.15.16.1''). * The LAN...") |
|||
| (2 intermediate revisions by 2 users not shown) | |||
| Line 5: | Line 5: | ||
== Assumptions == | == Assumptions == | ||
* You are operating | * You are operating your own Bondix server with the option to get additional public IPv4 addresses. | ||
* You have an additional IP address on the Bondix server (example: ''14.15.16.1''). | * You have an additional IP address on the Bondix server (example: '''''14.15.16.1'''''). | ||
* The LAN client behind the OpenWRT router has a private IP address like ''192.168. | * The LAN client behind the OpenWRT router has a private IP address like '''''192.168.5.213'''''. | ||
== Step 1: Configure additional IP address on the server == | == Step 1: Configure additional IP address on the server == | ||
Configure the additional IP address (e.g. ''14.15.16.1'') on the Bondix server based on the instructions of your server provider. | Configure the additional IP address (e.g. '''''14.15.16.1''''') on the Bondix server based on the instructions of your server provider. | ||
== Step 2: Create a new environment in the Bondix Server GUI == | == Step 2: Create a new environment in the Bondix Server GUI == | ||
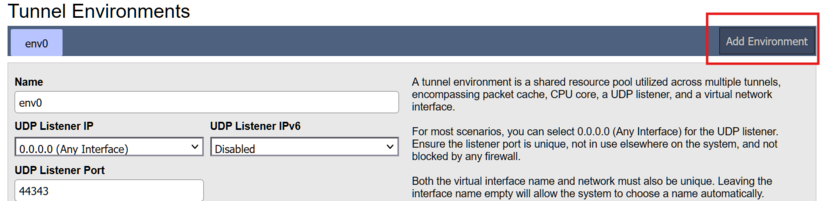
1. Log in to the Bondix server GUI. | 1. Log in to the Bondix server GUI. | ||
2. Create a **new environment**. | 2. Create a **new environment**. | ||
[[File:Addenv1.png| | [[File:Addenv1.png|none|825x825px]] | ||
| Line 24: | Line 25: | ||
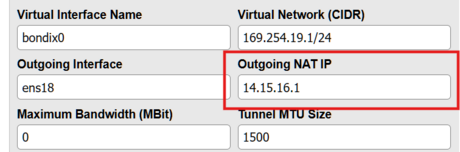
*'''Outgoing NAT IP''' = ''14.15.16.1'' | *'''Outgoing NAT IP''' = ''14.15.16.1'' | ||
[[File:Add_nat_ip.png|none|460x460px]] | |||
[[File: | |||
== Step 3: Add iptables rules on the Bondix server == | == Step 3: Add iptables rules on the Bondix server == | ||
| Line 33: | Line 32: | ||
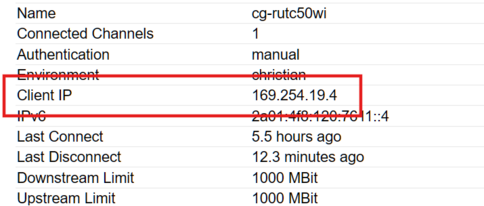
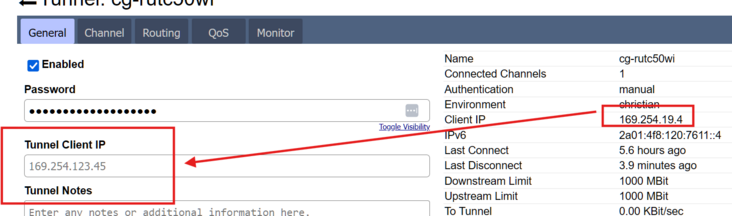
It will look like: ''169.254.xxx.xxx'' (example here: ''169.254.20.4''). | It will look like: ''169.254.xxx.xxx'' (example here: ''169.254.20.4''). | ||
[[File:Stats.png|frameless]] | [[File:Stats.png|frameless|484x484px]] | ||
Then add the following iptables rules on the Bondix server shell: | Then add the following iptables rules on the Bondix server shell: | ||
iptables -A PREROUTING -t nat -d 14.15.16.1 -j DNAT --to 169.254.xxx.xxx | '''''iptables -A PREROUTING -t nat -d 14.15.16.1 -j DNAT --to 169.254.xxx.xxx''''' | ||
iptables -A FORWARD -d 169.254.xxx.xxx -j ACCEPT | '''''iptables -A FORWARD -d 169.254.xxx.xxx -j ACCEPT''''' | ||
| Line 56: | Line 56: | ||
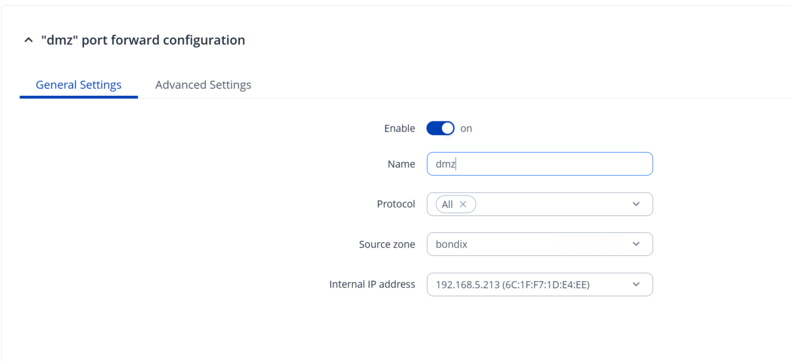
* From zone: **Bondix** | * From zone: **Bondix** | ||
* To IP: **192.168. | * To IP: **192.168.5.213** (LAN host) | ||
Set protocol to all as needed for your use case. | |||
Example screenshot from Teltonika: | Example screenshot from Teltonika: | ||
[[File:Dmz teltonika.png|frameless]] | [[File:Dmz teltonika.png|frameless|791x791px]] | ||
| Line 86: | Line 86: | ||
* '''Tunnel Client IP mask''' = ''169.254.19.4'' | * '''Tunnel Client IP mask''' = ''169.254.19.4'' | ||
[[File:Fixedip.png|frameless]] | [[File:Fixedip.png|frameless|732x732px]] | ||
This ensures the tunnel client always receives the IP address ''169.254.19.4''. | This ensures the tunnel client always receives the IP address ''169.254.19.4''. | ||
| Line 94: | Line 96: | ||
If you reserve the tunnel client IP (e.g. ''169.254.19.4''), update your iptables rules accordingly: | If you reserve the tunnel client IP (e.g. ''169.254.19.4''), update your iptables rules accordingly: | ||
'''iptables -A PREROUTING -t nat -d 14.15.16.1 -j DNAT --to 169.254.19.4''' | |||
iptables -A PREROUTING -t nat -d 14.15.16.1 -j DNAT --to 169.254.19.4 | |||
iptables -A FORWARD -d 169.254.19.4 -j ACCEPT | '''iptables -A FORWARD -d 169.254.19.4 -j ACCEPT''' | ||
With these settings: | With these settings: | ||
* Traffic to ''14.15.16.1'' on the Bondix server is DNATed to ''169.254.19.4'' (tunnel client). | * Traffic to ''14.15.16.1'' on the Bondix server is DNATed to '''''169.254.19.4''''' (tunnel client). | ||
* The OpenWRT client forwards this traffic from the Bondix zone to the LAN client ''192.168.5. | * The OpenWRT client forwards this traffic from the Bondix zone to the LAN client '''''192.168.5.213'''''. | ||
If you have further questions or special requirements, please contact support. | If you have further questions or special requirements, please contact support. | ||
Latest revision as of 14:33, 8 December 2025
DMZ and 1:1 NAT configuration with additional static, public IPv4 addresses on the Bondix server
This page describes how to forward traffic from a public IP on the Bondix server to a LAN host behind an Bondix client router using iptables and port forwarding.
Assumptions
- You are operating your own Bondix server with the option to get additional public IPv4 addresses.
- You have an additional IP address on the Bondix server (example: 14.15.16.1).
- The LAN client behind the OpenWRT router has a private IP address like 192.168.5.213.
Step 1: Configure additional IP address on the server
Configure the additional IP address (e.g. 14.15.16.1) on the Bondix server based on the instructions of your server provider.
Step 2: Create a new environment in the Bondix Server GUI
1. Log in to the Bondix server GUI.
2. Create a **new environment**.
3. In this environment, set:
- Outgoing NAT IP = 14.15.16.1
Step 3: Add iptables rules on the Bondix server
Determine the Bondix client interface IP in the tunnel (e.g. from the tunnel status page when the client is connected). It will look like: 169.254.xxx.xxx (example here: 169.254.20.4).
Then add the following iptables rules on the Bondix server shell:
iptables -A PREROUTING -t nat -d 14.15.16.1 -j DNAT --to 169.254.xxx.xxx
iptables -A FORWARD -d 169.254.xxx.xxx -j ACCEPT
Replace:
- 14.15.16.1 with your actual additional IP on the server (if different).
- 169.254.xxx.xxx with the actual tunnel client IP of the Bondix client.
Step 4: Configure port forwarding on the OpenWRT router
In the firewall of the Bondix client router:
1. Open the **Port Forwarding / Firewall** configuration. 2. Create a rule forwarding **all traffic from the Bondix zone** to the LAN client IP address:
- From zone: **Bondix**
- To IP: **192.168.5.213** (LAN host)
Set protocol to all as needed for your use case.
Example screenshot from Teltonika:
Step 5: Make iptables rules persistent
By default, iptables rules are **not persistent** and will be lost after a reboot.
To ensure the rules are always applied:
- Use a tool like iptables-persistent, **or**
- Create a Linux service / script that runs these iptables commands on boot.
Step 6: Reserve a fixed tunnel client IP (optional but recommended)
Once everything works, it is recommended to reserve the tunnel client IP for this specific Bondix tunnel client.
On the Bondix server:
1. Open the tunnel configuration for this client. 2. Set the desired fixed tunnel IP in the **Tunnel Client IP mask**, e.g.:
- Tunnel Client IP mask = 169.254.19.4
This ensures the tunnel client always receives the IP address 169.254.19.4.
Step 7: Final iptables rules with fixed tunnel IP
If you reserve the tunnel client IP (e.g. 169.254.19.4), update your iptables rules accordingly:
iptables -A PREROUTING -t nat -d 14.15.16.1 -j DNAT --to 169.254.19.4
iptables -A FORWARD -d 169.254.19.4 -j ACCEPT
With these settings:
- Traffic to 14.15.16.1 on the Bondix server is DNATed to 169.254.19.4 (tunnel client).
- The OpenWRT client forwards this traffic from the Bondix zone to the LAN client 192.168.5.213.
If you have further questions or special requirements, please contact support.