Quality of Service: Difference between revisions
No edit summary |
No edit summary |
||
| (18 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
With Bondix Quality of Service settings, you can apply different bonding rules for different types of traffic. Traffic can be differentiated via packet type, source, and/or destination IP. Bonding rules allow for setting priority or duplication to limiting bandwidth or optimizing for latency. | ==Basics== | ||
[[File:QoS Editor.png|thumb|right|The QoS editor with a default rule.]]With Bondix Quality of Service settings, you can apply different bonding rules for different types of traffic. Traffic can be differentiated via packet type, source, and/or destination IP. Bonding rules allow for setting priority or duplication to limiting bandwidth or optimizing for latency. | |||
===Server: QoS Presets=== | ===Server: QoS Presets=== | ||
On the server side, Bondix | On the server side, Bondix comes with a selection of QoS presets which can be used for quick configuration. In effect, Bondix QoS replaces Bondix Tunnel Presets. However, if QoS is to be initiated from the Client, make sure to choose "Custom QoS" in the Tunnel Presets of the General Settings. | ||
Here are the Server's QoS presets at a glance: | Here are the Server's QoS presets at a glance: | ||
| Line 30: | Line 30: | ||
|} | |} | ||
A QoS preset consists of one or more traffic groups (QoS group). When a client connects to a server, it sends along its desired QoS configuration which the server can either use or replace with a different configuration. The server also comes with a QoS preset editor which allows you to create custom presets that can be applied on multiple tunnels. | A QoS preset consists of one or more traffic groups (QoS group). When a client connects to a server, it sends along its desired QoS configuration which the server can either use or replace with a different configuration. The server also comes with a QoS preset editor which allows you to create custom presets that can be applied on multiple tunnels. | ||
<gallery widths=400px heights=260px> | |||
File:Bondix-123101-qos.png|thumb|QoS settings on Bondix Server | |||
File:Bondix-123101-tunnel-qos.png|thumb|QoS presets for Tunnels on Bondix Server | |||
File:Bondix-123101-qos-presets.png|thumb|QoS presets for Tunnels on Bondix Server, list | |||
</gallery> | |||
===Client & Server: Traffic Group=== | ===Client & Server: Traffic Group=== | ||
| Line 44: | Line 46: | ||
|- | |- | ||
| style="width: 150px" |Name | | style="width: 150px" |Name | ||
| | |This is where you give your traffic group a short descriptive name that ideally describes the type of traffic you want to assign to it. | ||
|- | |- | ||
|Score | |Score | ||
| Line 53: | Line 55: | ||
|- | |- | ||
|Latency Offset | |Latency Offset | ||
| | |This setting describes the maximum difference that is allowed between the interface with the lowest and the one with the highest latency. With this setting, you can exclude slow or unreliable lines should their latency become too high. A value of 0 means no limitation. | ||
|- | |- | ||
|Max Down (MBit) | |Max Down (MBit) | ||
| Line 113: | Line 115: | ||
Traffic matching rules are sorted by specificity. That means that the most specific rules are checked on first, the broadest rule is checked last. | Traffic matching rules are sorted by specificity. That means that the most specific rules are checked on first, the broadest rule is checked last. | ||
<gallery widths=400px heights=260px> | |||
File:Bondix-123101-qos.png|thumb|left|QoS settings on Bondix Server | |||
File:Tel-07045-network-bondixsane-qos.png|thumb|left|QoS settings on Bondix Client for Teltonika 07.04.5 | |||
File:Tel-07045-network-bondixsane-qos-detail.png|thumb|left|QoS settings on Bondix Client for Teltonika 07.04.5, Traffic Group detail | |||
</gallery> | |||
===Client: Teltonika=== | ===Client: Teltonika=== | ||
[[File:Teltonika Preset Selection.png|right]] | [[File:Teltonika Preset Selection.png|right]] | ||
If you want to use custom QoS settings on Teltonika routers, make sure that the preset is set to "Custom QoS" - otherwise | If you want to use custom QoS settings on Teltonika routers, make sure that the preset is set to "Custom QoS" and that the assigned server allows Client QoS settings - otherwise the server will override any Client QoS settings. You can verify this via the Status page. | ||
We recommend pushing QoS presets via the Bondix Server because then they're created and managed in a single place and don't have to manage the QoS settings on all routers individually. | |||
==Compatibility== | |||
Client and server are generally backwards compatible. When a legacy client connects to a QoS-enabled endpoint, the client can still apply its original tunnel preset (which is what QoS replaces). When a QoS-enabled client connects to a legacy server, it will always use the default "Bonding" tunnel preset, or the preset propagated by the legacy server. | Client and server are generally backwards compatible. When a legacy client connects to a QoS-enabled endpoint, the client can still apply its original tunnel preset (which is what QoS replaces). When a QoS-enabled client connects to a legacy server, it will always use the default "Bonding" tunnel preset, or the preset propagated by the legacy server. | ||
== Best Practices == | |||
* Always create a default rule that matches to any traffic. Traffic without an appropriate matching rule will still be transmitted but performance results may vary. | * Always create a default rule that matches to any traffic. Traffic without an appropriate matching rule will still be transmitted but performance results may vary. | ||
* BondingProxy uses ''iptables'' rules to redirect matching TCP traffic. To exclude certain traffic from BondingProxy, create a new group with matching rules and the proxy disabled. This will create appropiate exclusion rules for ''iptables''. | * BondingProxy uses ''iptables'' rules to redirect matching TCP traffic. To exclude certain traffic from BondingProxy, create a new group with matching rules and the proxy disabled. This will create appropiate exclusion rules for ''iptables''. | ||
Latest revision as of 12:23, 9 December 2025
Basics
With Bondix Quality of Service settings, you can apply different bonding rules for different types of traffic. Traffic can be differentiated via packet type, source, and/or destination IP. Bonding rules allow for setting priority or duplication to limiting bandwidth or optimizing for latency.
Server: QoS Presets
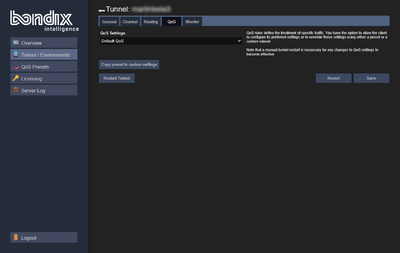
On the server side, Bondix comes with a selection of QoS presets which can be used for quick configuration. In effect, Bondix QoS replaces Bondix Tunnel Presets. However, if QoS is to be initiated from the Client, make sure to choose "Custom QoS" in the Tunnel Presets of the General Settings.
Here are the Server's QoS presets at a glance:
| Preset | Description |
|---|---|
| Bonding | This is the default preset - bonding over any interface with BondingProxy enabled. |
| Bonding (No Proxy) | Bonding with BondingProxy disabled. |
| Packet Duplication | Default Bonding with packet duplication (1x) enabled. |
| Seamless failover | Only use one interface as indicated by channel priority or latency. |
| Satellite | A preset for satellite scenarios. Satellite is only used for HTTP(S) traffic, except when no other interfaces are available. |
| Default QoS | A more sophisticated preset including a priority rule for DNS traffic, VoIP and online meetings. |
A QoS preset consists of one or more traffic groups (QoS group). When a client connects to a server, it sends along its desired QoS configuration which the server can either use or replace with a different configuration. The server also comes with a QoS preset editor which allows you to create custom presets that can be applied on multiple tunnels.
Client & Server: Traffic Group
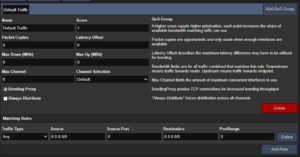
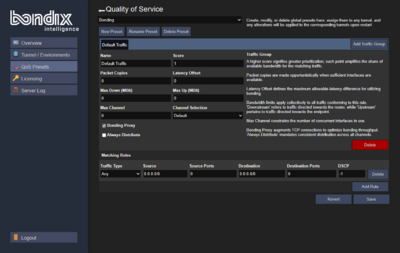
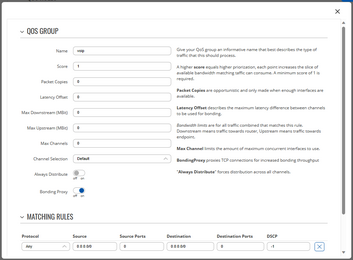
A traffic group (QoS group) consists of a ruleset of how traffic should be handled, and a list of matching traffic types to which these rules shoule be applied to.
Group Settings
| Property | Description |
|---|---|
| Name | This is where you give your traffic group a short descriptive name that ideally describes the type of traffic you want to assign to it. |
| Score | The group's score determines how often it gets the chance to send out data. The minimum value is 1, each additional score point gives the group a bigger slice of available data. Groups with higher score also get to write their data first. View this as a type of priority setting. |
| Packet Copies | This value defines how many copies of each packet should be made. A value of 0 means no duplication, a value of 1 means single duplication, and so on. Packet Copies are opportunistic: If not enough interfaces are available to send the amount of configured copies, less copies will be made. |
| Latency Offset | This setting describes the maximum difference that is allowed between the interface with the lowest and the one with the highest latency. With this setting, you can exclude slow or unreliable lines should their latency become too high. A value of 0 means no limitation. |
| Max Down (MBit) | This value defines the maximum bandwidth allowed downstream in MBit. Downstream always refers to traffic sent from the server to the client. A value of 0 means no limitation. |
| Max Up (MBit) | This value defines the maximum bandwidth allowed upstream in MBit. Upstream always refers to traffic sent from the client to the server. A value of 0 means no limitation. |
| Max Channel | This value sets the maximum number of channels that should be used at once for this group. A value of 0 means no limit. |
| Channel Selection | Here, you can define how channels are selected. These are the possible options:
|
| Bonding Proxy | If enabled, matching TCP traffic will be bonded using BondingProxy which optimizes bonding throughput and efficiency. |
| Always Distribute | If enabled, traffic is always spread through all interfaces. This is disabled by default as it usually introduces unnecessary jitter but may be beneficial if you're looking to spread traffic evenly across multiple interfaces. |
Matching Rules
Matching rules describe the type of traffic you want to assign to a group.
| Property | Description |
|---|---|
| Traffic Type | Possible options:
|
| Source | Here, you define the source IP network in CIDR notation. In order to match properly, make sure to disable masquerading on the client. A value of "0.0.0.0/0" means traffic from any source. |
| Source Port | Here, you define the source port. This can either be a single value (e.g. "80") or a range (e.g. "22-23"). A value of 0 means any port. |
| Destination | Here, you give the destination IP network in CIDR notation. For individual IPs, make sure to include the network prefix /32. A value of "0.0.0.0/0" means traffic to any destination. |
| Destination Port | Here, you give the destination port. This can either be a single value (e.g. "80") or a range (e.g. "22-23"). A value of 0 means any port. |
| DSCP | Here, you specify the DSCP Differentiated Services Code Point value. A value of -1 means that packets with any DSCP value will match. This value is ignored in combination with Bonding Proxy. |
Traffic matching rules are sorted by specificity. That means that the most specific rules are checked on first, the broadest rule is checked last.
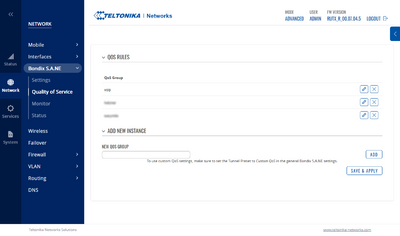
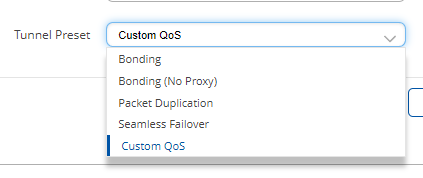
Client: Teltonika
If you want to use custom QoS settings on Teltonika routers, make sure that the preset is set to "Custom QoS" and that the assigned server allows Client QoS settings - otherwise the server will override any Client QoS settings. You can verify this via the Status page.
We recommend pushing QoS presets via the Bondix Server because then they're created and managed in a single place and don't have to manage the QoS settings on all routers individually.
Compatibility
Client and server are generally backwards compatible. When a legacy client connects to a QoS-enabled endpoint, the client can still apply its original tunnel preset (which is what QoS replaces). When a QoS-enabled client connects to a legacy server, it will always use the default "Bonding" tunnel preset, or the preset propagated by the legacy server.
Best Practices
- Always create a default rule that matches to any traffic. Traffic without an appropriate matching rule will still be transmitted but performance results may vary.
- BondingProxy uses iptables rules to redirect matching TCP traffic. To exclude certain traffic from BondingProxy, create a new group with matching rules and the proxy disabled. This will create appropiate exclusion rules for iptables.